- Home
- Basic Policies on Personal Information and Information Security
- Information security measures
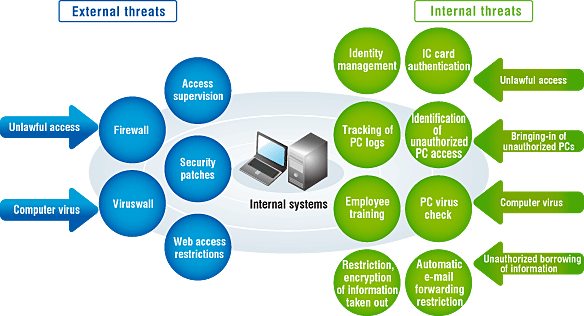
Information security measures
Each fiscal year, security practices are improved and plans written based on the state of activities the previous fiscal year. Information security measures are then taken accordingly. Major measures are as follows.
1. Organization and structure
- Establishment of Information Security Committee as a lateral organization whose membership comprises the heads of all J-POWER head-office divisions
- General Affairs Department's IT Promotion Office, appointed to provide general management of information security, promotes the development of rules and the implementation of specific measures
- Quick response by risk management system at any time an information security incident arises
- Joint assessment by all J-POWER Group companies of information security status at individual companies, and implementation of improvements
2.Personal measures
With cooperation from JP Business Service Corporation, a Group company that is responsible for information system operations, the J-POWER Group is taking the following measures for training and instruction relating to information security at Group companies.
- Instruction and training including e-learning and seminars is conducted for all Group employees
- Periodic reports concerning the state of information security are prepared and concerned personnel are informed and instructed about information security each quarter
- Information security patrols are conducted at power stations and awareness-raising programs are conducted for maintenance personnel
- Training is conducted based on scenarios involving the occurrence of information security incidents
3.Physical measures
- Locking control (head office) when people enter or leave the premises, by means of IC cards (for employee identification)
- Separation of business areas from meeting and reception space
4.Technical measures
- Prevention of unlawful intrusion through the Internet
- Access management (user authentication) for all business systems by means of IC cards (for employee identification)
- Approval by senior staff for removal of electronic information, and encryption of files
- Encryption of e-mail attached files
- Creating password to PCs for business trip
- Collection and analysis of various operating logs and creation of reports
J-POWER Group Information Security Countermeasures